Application Layer
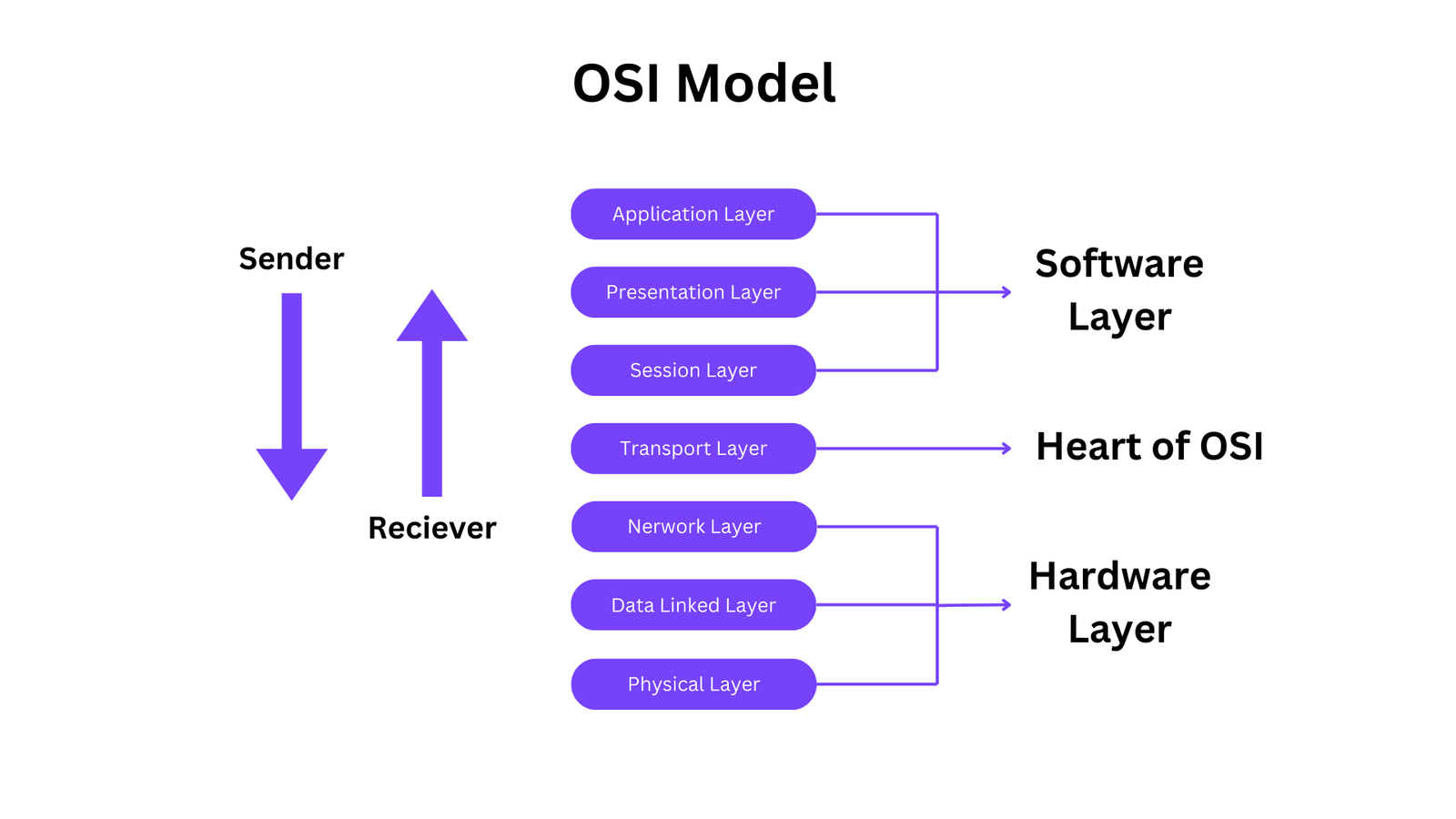
The application layer, in the context of computer networking, refers to the topmost layer of the OSI (Open Systems Interconnection) model or the TCP/IP (Transmission Control Protocol/Internet Protocol) model. It serves as the interface between network-aware applications and the underlying network infrastructure.

This layer also makes a request to its bottom layer, which is presentation layer for receiving various types of information from it. The Application Layer interface directly interacts with application and provides common web application services. This layer is basically highest level of open system, which provides services directly for application process.
The application layer provides services and protocols that enable communication between different software applications running on devices connected to a network. It abstracts the complexities of lower-level networking protocols and facilitates high-level communication, data exchange, and interaction between end-users or applications.
Key responsibilities of the application layer include:
- Data Representation and Encryption:
- Ensuring that data is presented in a format that is understandable by the receiving application. This may involve data compression, encryption, and formatting.
- Communication Services:
- Providing various communication services such as email, file transfer, remote login, and web browsing. Protocols like SMTP (Simple Mail Transfer Protocol), FTP (File Transfer Protocol), SSH (Secure Shell), and HTTP (Hypertext Transfer Protocol) operate at this layer.
- Application Layer Protocols:
- Supporting application layer protocols that define the rules and conventions for communication between applications. Examples include HTTP, SMTP, POP3 (Post Office Protocol version 3), IMAP (Internet Message Access Protocol), DNS (Domain Name System), and SNMP (Simple Network Management Protocol).
- Client-Server Communication:
- Facilitating communication between clients and servers. In client-server architectures, the application layer on the client side interacts with the application layer on the server side to request and receive services.
- User Authentication and Authorization:
- Providing mechanisms for user authentication and authorization. This may involve login procedures, password authentication, and access control.
- Error Handling and Recovery:
- Handling errors that occur during data transmission and implementing mechanisms for error recovery and retransmission if necessary.
- Application Interfaces:
- Providing interfaces and APIs (Application Programming Interfaces) that allow applications to access network services and communicate with other applications effectively.
Application Layer Protocols
The application layer of the OSI model encompasses a wide range of protocols and services that enable communication between networked applications. Here are some of the most common application layer protocols:
- Hypertext Transfer Protocol (HTTP):
- HTTP is used for transmitting hypermedia documents, such as HTML files, over the World Wide Web. It defines how web browsers and web servers communicate to request and deliver web pages and other resources.
- Simple Mail Transfer Protocol (SMTP):
- SMTP is used for sending and receiving email messages between mail servers. It handles the transfer of email messages from the sender’s mail server to the recipient’s mail server.
- Post Office Protocol version 3 (POP3):
- POP3 is an email retrieval protocol used by email clients to retrieve messages from a mail server. It allows users to download emails from the server to their local device for reading and storage.
- Internet Message Access Protocol (IMAP):
- IMAP is another email retrieval protocol that allows users to access and manage email messages stored on a remote mail server. Unlike POP3, IMAP keeps messages on the server and provides more advanced features for organizing and searching emails.
- File Transfer Protocol (FTP):
- FTP is used for transferring files between a client and a server over a network. It provides commands for uploading, downloading, renaming, and deleting files on a remote server.
- Simple Network Management Protocol (SNMP):
- SNMP is used for managing and monitoring network devices, such as routers, switches, and servers. It allows network administrators to collect and analyze information about device performance, status, and configuration.
- Domain Name System (DNS):
- DNS is used for translating domain names (e.g., www.example.com) into IP addresses (e.g., 192.0.2.1) and vice versa. It enables users to access websites and other network resources using human-readable domain names.
- Dynamic Host Configuration Protocol (DHCP):
- DHCP is used for dynamically assigning IP addresses and other network configuration parameters to devices on a network. It automates the process of network configuration, making it easier to manage large networks.
- Secure Shell (SSH):
- SSH is a secure network protocol used for remote login and command execution on a remote device. It provides encrypted communication between the client and server, protecting sensitive information from eavesdropping and tampering.
- Remote Desktop Protocol (RDP):
- RDP is used for accessing and controlling a remote desktop or graphical user interface (GUI) over a network. It allows users to remotely connect to and interact with a desktop environment on another computer.
Working of Application Layer
The application layer in a computer network works by facilitating communication between different software applications running on devices connected to the network. Here’s a general overview of how it works:
- Interface with User Applications:
- The application layer provides an interface for user applications to access network services. Applications interact with the application layer through APIs (Application Programming Interfaces) or protocols specifically designed for communication at this layer.
- Protocol Selection and Configuration:
- When an application needs to communicate with another application over the network, the application layer selects the appropriate communication protocol based on the requirements of the application and the network environment. For example, if a web browser wants to retrieve a web page from a server, it may use the HTTP (Hypertext Transfer Protocol) protocol.
- Data Preparation and Formatting:
- Before data is transmitted over the network, the application layer prepares and formats the data according to the requirements of the chosen protocol. This may involve tasks such as data compression, encryption, and encapsulation into packets suitable for transmission.
- Initiating Communication:
- Once the data is ready, the application layer initiates communication with the corresponding application on another device. This involves establishing a connection, if necessary, and sending the data packets over the network.
- Protocol Handling and Processing:
- As data packets are transmitted over the network, the application layer on the receiving end receives and processes them according to the chosen protocol. It performs tasks such as packet disassembly, data decryption, and error checking to ensure the integrity and correctness of the received data.
- Delivering Data to User Applications:
- Once the data packets are processed, the application layer delivers the data to the appropriate user application running on the receiving device. This enables the application to interpret and utilize the received data for further processing or display to the user.
- Handling User Authentication and Authorization:
- In cases where user authentication and authorization are required, the application layer facilitates these processes by interacting with authentication servers and verifying user credentials before allowing access to network resources or services.
- Error Handling and Recovery:
- Throughout the communication process, the application layer handles errors and ensures reliable data transmission. This may involve detecting and retransmitting lost or corrupted data packets, as well as implementing error correction mechanisms to maintain data integrity.
Services of Application Layer
The application layer in computer networks provides a wide range of services to support communication between networked devices and enable the exchange of data between applications. Some of the key services offered by the application layer include:
- Email Services:
- The application layer supports email services, allowing users to send, receive, and manage electronic messages over the network. Protocols such as SMTP (Simple Mail Transfer Protocol), POP3 (Post Office Protocol version 3), and IMAP (Internet Message Access Protocol) are commonly used for email communication.
- File Transfer Services:
- Application layer protocols such as FTP (File Transfer Protocol) and SFTP (SSH File Transfer Protocol) facilitate the transfer of files between devices connected to the network. These services enable users to upload, download, and manage files stored on remote servers.
- Web Services:
- The application layer supports web services, enabling users to access and interact with websites and web applications over the internet. Protocols such as HTTP (Hypertext Transfer Protocol) and HTTPS (HTTP Secure) are used for communication between web clients (e.g., web browsers) and web servers.
- Remote Access Services:
- Application layer protocols such as SSH (Secure Shell) and Telnet enable remote access to networked devices and systems. These services allow users to log in to remote servers and access command-line interfaces or graphical user interfaces for system administration and management.
- Domain Name Services (DNS):
- The application layer includes DNS services, which translate domain names (e.g., www.example.com) into IP addresses (e.g., 192.0.2.1) and vice versa. DNS resolution is essential for identifying and accessing network resources by their domain names.
- Directory Services:
- Application layer directory services, such as LDAP (Lightweight Directory Access Protocol), provide a centralized directory of network resources and user information. These services support authentication, authorization, and user management across distributed network environments.
- Network Management Services:
- The application layer supports network management services, allowing administrators to monitor, configure, and troubleshoot network devices and resources. Protocols such as SNMP (Simple Network Management Protocol) enable the collection and exchange of network management information.
- Real-Time Communication Services:
- Application layer protocols such as SIP (Session Initiation Protocol) and RTP (Real-time Transport Protocol) support real-time communication services, including voice and video calls, conferencing, and multimedia streaming over IP networks.
- Database Services:
- The application layer includes database services, enabling applications to access and manipulate databases stored on remote servers. Protocols such as ODBC (Open Database Connectivity) and JDBC (Java Database Connectivity) facilitate database connectivity and query execution.
- Collaboration Services:
- The application layer supports collaboration services, enabling users to work together on shared documents, projects, and tasks. Examples include collaborative document editing platforms, project management tools, and virtual whiteboards.
What is the application layer in computer networks?
The application layer is the topmost layer of the OSI (Open Systems Interconnection) model and the TCP/IP (Transmission Control Protocol/Internet Protocol) model. It provides network services directly to end-users or applications running on those end-user devices.
What are some common protocols used in the application layer?
Some common protocols used in the application layer include HTTP (Hypertext Transfer Protocol), SMTP (Simple Mail Transfer Protocol), FTP (File Transfer Protocol), DNS (Domain Name System), DHCP (Dynamic Host Configuration Protocol), and SNMP (Simple Network Management Protocol).
What is the role of the application layer in networking?
The application layer facilitates communication between different applications or processes running on separate networked devices. It provides services such as email, file transfer, remote login, web browsing, and network management. It also handles data representation, encryption, user authentication, and error handling.
What is the difference between HTTP and HTTPS?
HTTP (Hypertext Transfer Protocol) is a protocol used for transmitting hypermedia documents, such as web pages, over the World Wide Web. HTTPS (HTTP Secure) is a secure version of HTTP that uses encryption to protect data transmitted between the client and server, ensuring confidentiality and integrity.