OSI Model of Computer Network
What is OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework used to understand and describe how different networking protocols and technologies interact with each other. It divides network communication into seven distinct layers, each responsible for specific functions.
- OSI consists of seven layers, and each layer performs a particular network function.
- OSI model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered as an architectural model for the inter-computer communications.
- OSI model divides the whole task into seven smaller and manageable tasks. Each layer is assigned a particular task.
- Each layer is self-contained, so that task assigned to each layer can be performed independently.
7 Layers of OSI Model
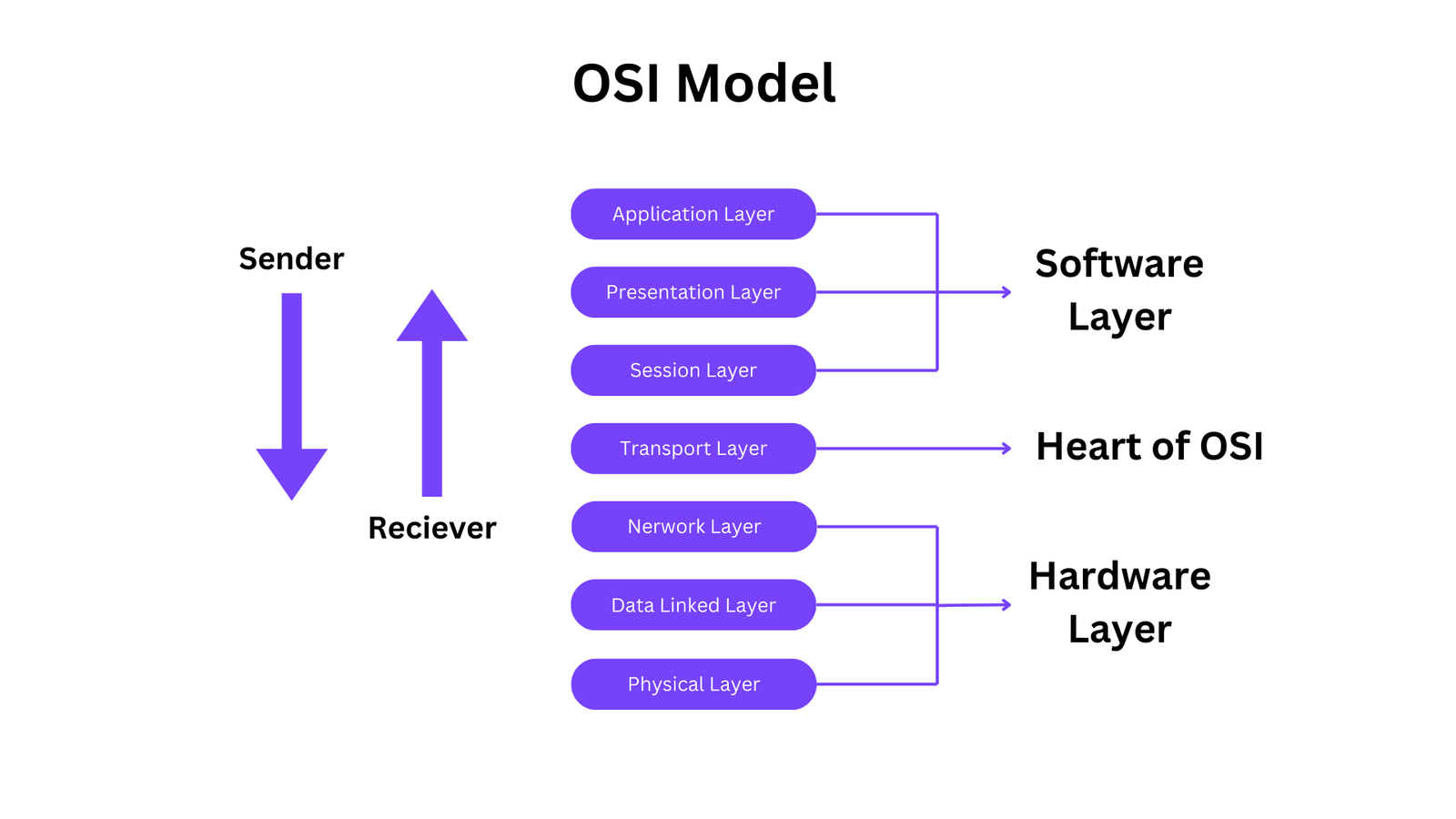
Physical Layer
The physical layer is responsible for transmitting raw data bits over a physical medium, defining the characteristics of the physical connection, and converting digital data into signals suitable for transmission over the medium.
Functions:
- Concerned with transmitting raw data bits over a physical medium.
- Defines the characteristics of the physical connection, including voltage levels, cable types, and data rates.
- Converts digital data into signals suitable for transmission over the physical medium.
- Manages physical connections and controls the transmission of data.
Data Link Layer
The data link layer provides error-free transfer of data frames between adjacent nodes over a physical link, handles framing, error detection, and correction, and controls access to the physical medium.
- Framing:
- The Data Link Layer encapsulates network layer packets into data frames for transmission over the physical medium. It delineates where one frame of data ends and the next one begins, allowing devices to identify and extract individual frames.
- Error Detection and Correction:
- This layer is responsible for detecting errors that may occur during transmission, typically through techniques like checksums or CRC (Cyclic Redundancy Check). If errors are detected, the Data Link Layer may attempt to correct them using mechanisms such as automatic repeat request (ARQ) or forward error correction (FEC).
- Flow Control:
- The Data Link Layer manages the flow of data between devices to ensure that the sender does not overwhelm the receiver with data. It implements flow control mechanisms to regulate the rate at which data is transmitted, preventing buffer overflows and data loss.
- Access Control:
- In shared media networks, such as Ethernet, the Data Link Layer controls access to the physical medium to prevent data collisions. It employs protocols like CSMA/CD (Carrier Sense Multiple Access with Collision Detection) or CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) to manage access to the transmission medium and coordinate transmissions between devices.
- Addressing:
- The Data Link Layer assigns physical addresses, such as MAC (Media Access Control) addresses, to network interfaces to uniquely identify devices on the same local network. MAC addresses are used for addressing within the same network segment and facilitate the delivery of frames to the correct destination.
- Media Access Control:
- In addition to access control mechanisms for shared media networks, the Data Link Layer may implement protocols specific to the type of physical medium being used (e.g., Ethernet, Wi-Fi, or PPP). These protocols govern how devices access and utilize the physical medium for communication.
Network Layer
The network layer is responsible for routing and forwarding data packets between different networks, using logical addressing (such as IP addresses) to identify devices, determining the best path for data to travel, and managing congestion control.
Functions:
- Responsible for routing and forwarding data packets between different networks.
- Uses logical addressing (such as IP addresses) to identify devices on the network.
- Determines the best path for data to travel from the source to the destination across multiple network hops.
- Handles congestion control and network addressing.
Transport Layer
The transport layer ensures reliable and orderly delivery of data between source and destination hosts, handling error detection, retransmission of lost data, and flow control, and managing data segmentation and reassembly.
Functions:
- Provides end-to-end communication between source and destination hosts.
- Ensures reliable and orderly delivery of data by handling error detection, retransmission of lost data, and flow control.
- Manages data segmentation and reassembly, breaking large chunks of data into smaller segments for transmission and reassembling them at the receiving end.
- Offers connection-oriented (e.g., TCP) and connectionless (e.g., UDP) communication services.
Session Layer
The session layer establishes, maintains, and synchronizes communication sessions between applications on different devices, allowing for the coordination of data exchange and managing dialog control between applications.
Functions:
- Establishes, maintains, and synchronizes communication sessions between applications on different devices.
- Allows for the coordination of data exchange and manages dialog control between applications.
- Provides services such as session establishment, data exchange, and session termination.
Presentation Layer
The presentation layer handles data translation, encryption, and compression, ensuring that data sent from one system can be properly interpreted by the receiving system, and deals with issues such as data format conversion and data encryption/decryption.
- Handles data translation, encryption, and compression to ensure that data sent from one system can be properly interpreted by the receiving system.
- Deals with issues such as data format conversion, character encoding, and data encryption/decryption.
- Provides a common representation of data exchanged between applications, regardless of differences in data formats and encoding schemes.
Application Layer
The application layer provides network services directly to end-users and application processes, implements protocols for various network services such as email, file transfer, and remote login, and manages user authentication, authorization, and data exchange between applications.
Functions:
- Provides network services directly to end-users and application processes.
- Implements protocols for various network services such as email (e.g., SMTP), file transfer (e.g., FTP), and remote login (e.g., SSH).
- Enables interaction between applications and the network, allowing users to access network resources and services.
- Manages user authentication, authorization, and data exchange between applications.
Frequently Ask Questions
What is the OSI model?
The OSI model, short for Open Systems Interconnection model, is a conceptual framework used to understand and describe how different networking protocols and technologies interact with each other. It consists of seven layers, each responsible for specific functions in data communication.
What are some examples of protocols at each layer of the OSI model?
Physical Layer: Ethernet, Wi-Fi, Fiber Optics
Data Link Layer: Ethernet (IEEE 802.3), PPP (Point-to-Point Protocol)
Network Layer: IP (Internet Protocol), ICMP (Internet Control Message Protocol)
Transport Layer: TCP (Transmission Control Protocol), UDP (User Datagram Protocol)
Session Layer: NetBIOS, RPC (Remote Procedure Call)
Presentation Layer: ASCII, JPEG, SSL (Secure Sockets Layer)
Application Layer: HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), DNS (Domain Name System)
Why is the OSI model important?
The OSI model provides a standardized way to understand and discuss how different networking technologies and protocols interact. It helps in troubleshooting network issues, designing new network systems, and ensuring interoperability between different networking devices and software.
Add a Comment